

Researchers from the Citizen Lab have introduced a paper increasing the risk mannequin of a 2021 assault impacting fashionable VPN software program dubbed “Port Shadow.”
Introduced by Benjamin Mixon-Baca on the Privateness Enhancing Applied sciences Symposium (PETS) 2024 in Bristol, UK, the paper particulars how the “Port Shadow” assault, and the underlying vulnerability which is tracked as CVE-2021-3773, still affects major VPN protocols akin to OpenVPN, WireGuard, and OpenConnect on Linux and FreeBSD techniques.
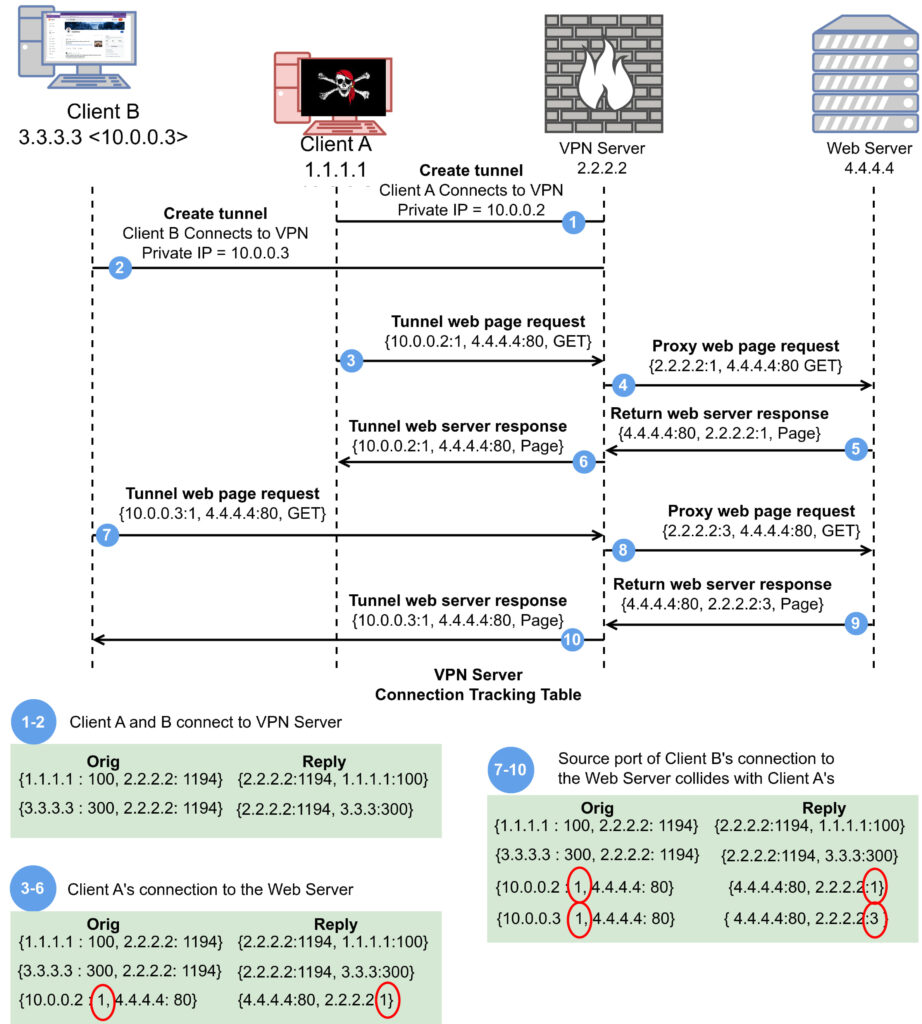
The Port Shadow assault
The port shadow assault, first documented roughly three years ago, issues an exploit that considerably extends the attain and capabilities of attackers concentrating on VPN customers. At its core, this assault manipulates the shared sources on a VPN server, particularly, the ports utilized by the connection monitoring framework.
The mechanism of the assault compromises particular parts as listed under:
- Shared useful resource exploitation: In a typical VPN setup, a number of customers connect with the identical VPN server, and every connection is assigned a novel port. These ports are a part of the connection monitoring framework, which manages how information packets are routed between the customers’ units and the web.
- Crafting malicious packets: An attacker, who can also be related to the identical VPN server, can craft malicious information packets. These packets are designed to take advantage of the connection monitoring framework by mimicking authentic site visitors and manipulating the shared port assignments.
- Hijacking connections: By rigorously injecting these crafted packets, the attacker can redirect site visitors meant for an additional person to themselves. This successfully makes the attacker an in-path router, intercepting and doubtlessly altering the info being transmitted between the sufferer and the VPN server.
- Deanonymizing and interfering: As soon as on this place, the attacker can deanonymize the sufferer’s connection, carry out port scans, inject malicious DNS responses, and even redirect the sufferer to malicious web sites. The assault shouldn’t be restricted by the attacker’s bodily location however fairly by their capacity to hook up with the identical VPN server because the sufferer.

Citizen Lab
“We discovered that Linux/Netfilter + (OpenVPN and WireGuard), which a big fraction of VPN companies use, has the very best susceptibility to those assaults no matter shopper platform (PC, Android, and iOS).”
Citizen Lab
Danger mitigation
The researchers demonstrated that VPN servers utilizing OpenVPN or WireGuard immediately can nonetheless be exploited by means of the port shadow assault, permitting attackers to hijack connections, inject malicious packets, or carry out denial-of-service assaults.
Neither OpenVPN nor WireGuard have addressed the dangers that come up from CVE-2021-3773 as a result of the flaw isn’t a part of their software program stacks. The Linux kernel staff did try to repair the problem in December 2021, however the fixing commit was reverted because of backwards compatibility points in March 2022, and the flaw stays unaddressed since them. Citizen Lab says CVE-2021-3773 continues to be exploitable in the newest Linux kernel model.
To mitigate the chance, VPN distributors ought to randomize supply port choice to scale back predictability in port task, implement particular firewall guidelines that block unauthorized port utilization, and restrict concurrent connections to decrease numbers.
For finish customers, because the found flaws that make the port shadow assault doable lie on the server and never the shopper app, there’s solely a bit of they’ll do to scale back the chance. The researchers advocate connecting to personal VPN servers or utilizing non-vulnerable protocols like Shadowsocks or Tor. In the end, it’s as much as the customers to do due diligence to make sure their software program is protected towards CVE-2021-3773.
VPN companies like NordVPN, ExpressVPN, and Surfshark sometimes make the most of the talked about protocols, however CitizenLabs notes that they’re not weak to CVE-2021-3773. It’s unclear what the standing is with different VPN distributors, so customers are really useful to ask their suppliers instantly about applied fixes and mitigations.













