

ESET researchers have uncovered a zero-day vulnerability named “EvilVideo” that targets Telegram for Android, enabling attackers to ship malicious payloads disguised as video recordsdata.
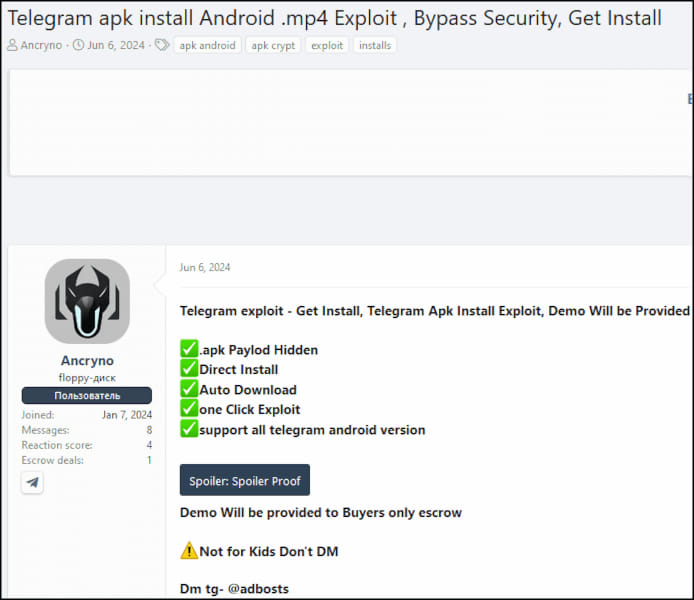
On June 6, 2024, a zero-day exploit focusing on Telegram for Android appeared on the market on an underground discussion board. This exploit, leveraging a vulnerability named “EvilVideo,” was examined by ESET researcher Lukas Stefanko, who confirmed it permits attackers to distribute malicious Android payloads via Telegram channels, teams, and chats, masquerading them as multimedia recordsdata.

ESET
The exploit vendor showcased screenshots and a video demonstrating the exploit in a public Telegram channel. On June 26, 2024, ESET reported the vulnerability to Telegram. The crew at Telegram responded by releasing a patch on July 11, 2024, in model 10.14.5 of the app.
EvilVideo breakdown
The EvilVideo exploit impacts Telegram for Android variations 10.14.4 and earlier. It possible makes use of the Telegram API to craft malicious multimedia recordsdata that seem as video previews in chats. Upon receiving these recordsdata, customers with computerized media obtain enabled would inadvertently obtain the malicious payload.
As soon as the person makes an attempt to play the video, Telegram shows a message indicating it can not play the file and suggests utilizing an exterior participant. If the person follows this suggestion, they’re prompted to put in a malicious app disguised as an exterior participant. This app, detected as Android/Spy.SpyMax.T, is downloaded as an obvious video file with an .apk extension. The exploit’s nature misleads the Telegram preview into displaying the file as a video, though it’s an APK.
The exploit particularly targets Telegram for Android and has no affect on Telegram Net or Telegram Desktop purchasers. In ESET’s assessments on the latter two, the payloads have been handled as multimedia recordsdata, stopping the exploit from functioning.
Whereas the precise id of the menace actor stays unknown, ESET discovered that the identical particular person has been promoting an Android cryptor-as-a-service on the identical discussion board since January 2024. This service claims to be absolutely undetectable, although ESET has not examined these claims.
Telegram’s decision
Following the invention of EvilVideo on June 26, 2024, ESET reported the problem to Telegram. Though initially unresponsive, Telegram’s crew confirmed the investigation on July 4, 2024, and issued a repair with the discharge of model 10.14.5 on July 11, 2024. The up to date model accurately identifies shared recordsdata as purposes, stopping the exploit from deceiving customers.
If you’re utilizing Telegram on Android, you’re suggested to improve to the most recent model as quickly as potential. In case you’ve just lately obtained video recordsdata resulting in putting in APKs by way of Telegram, think about your self breached and instantly provoke a clean-up process. It’s unknown for a way lengthy this zero-day has been accessible to the exploit vendor and what number of cybercriminals might need been leveraging it in assaults.













